Cloud architectures have completely redefined the way we do business, especially at the enterprise level. Teams that build software themselves rely more and more on the support of third-party applications, allowing them to conduct business more efficiently by focusing on their core product or service and delegating the rest to the companies and products better-suited to resolving those issues.
For the workers inside these companies the new tools are great, but they come at the cost of increased complexity: more logins to remember, and more users and credentials spread around the internet, the use of many different applications means that they have to remember many different account credentials and login procedures. It also creates a greater number of user accounts spread all over the internet, which not only exposes a greater risk of security breaches, but also makes the lives of IT managers even more complicated.
To overcome these problems, organizations began adopting centralized identity systems. Today we’re introducing our support for SAML, the login protocol that’s flexible, secure, user-friendly, and widely adopted across the enterprise world. But before we dive into all of the benefits that SAML provides, let’s learn a bit more about how it works.
What is SAML and how it works
The Security Services Technical Committee of OASIS defines the “Security Assertion Markup Language” (SAML) as:
“…an XML-based framework for communicating user authentication, entitlement, and attribute information. As its name suggests, SAML allows business entities to make assertions regarding the identity, attributes, and entitlements of a subject (an entity that is often a human user) to other entities, such as a partner company or another enterprise application.”
Source
In other words, SAML allows services to authenticate and assert the identity of a user on one system and send that information to a different system. This means that third party applications don’t need to have access to a user’s actual credentials in order to assert the authenticity of that user.
To understand how SAML works, we need to define the stakeholders involved in SAML:
- The User: the client attempting to access a third party application.
- The Identity Provider (IdP): the system that can assert the identity of a User.
- The Service Provider (SP): the system that provides the end application.
SAML is flexible, and these stakeholders can interact in a few different ways:
SP-Initiated Flow
- The User tries to access an application hosted by the SP.
- The SP will issue an authorization request to the IdP to assert the identity of the User.
- The IdP verifies the user’s credentials and issues a SAML Response to the SP.

IdP-Initiated Flow
- The User signs into their Company Web Portal.
- The User accesses the application hosted by the SP with one click.
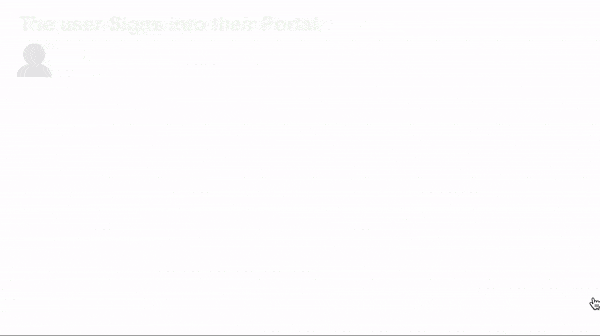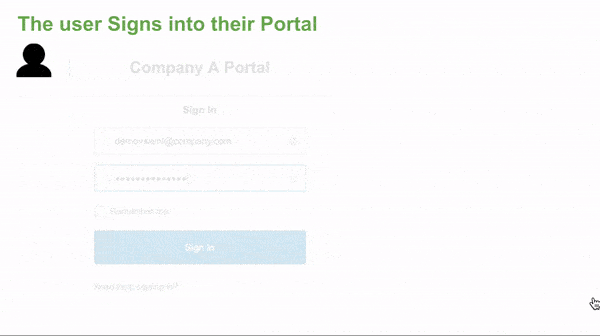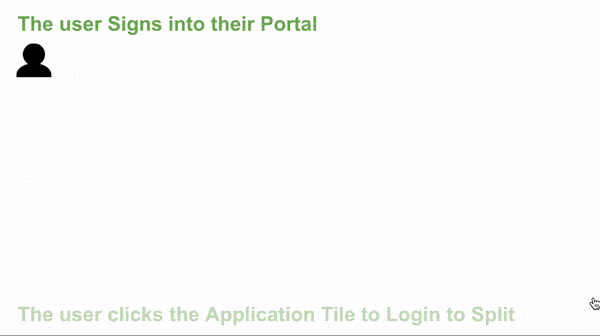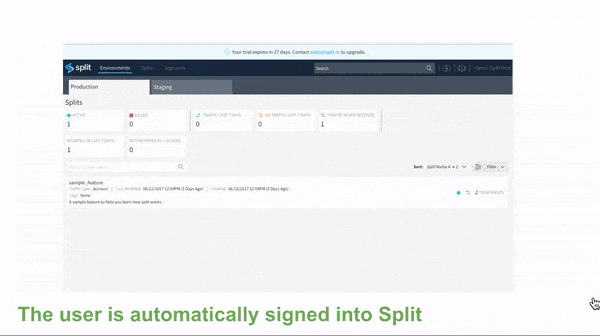
Why SAML is important
From security to simplicity, the benefits of SAML are myriad:
- Increases customer satisfaction by eliminating multiple passwords from different third party applications and allowing employees to access other applications with a single click (Single Sign On).
- Enhances security by pushing the management of identities to the identity provider. Customers control the users who access our platform through their own directory management.
- Identity Providers no longer need to maintain and synchronize directories with Service Providers, reducing administrative costs on both ends.
SAML implementation at Split
Split’s implementation of SAML is simple but robust. We support both IdP-Initiated Flows and SP-Initiated Flows. For the IdP Initiated Flow we support POSTS XML Assertions. For the IdP Initiated Flow, Split will issue a Redirect Authorization Request.
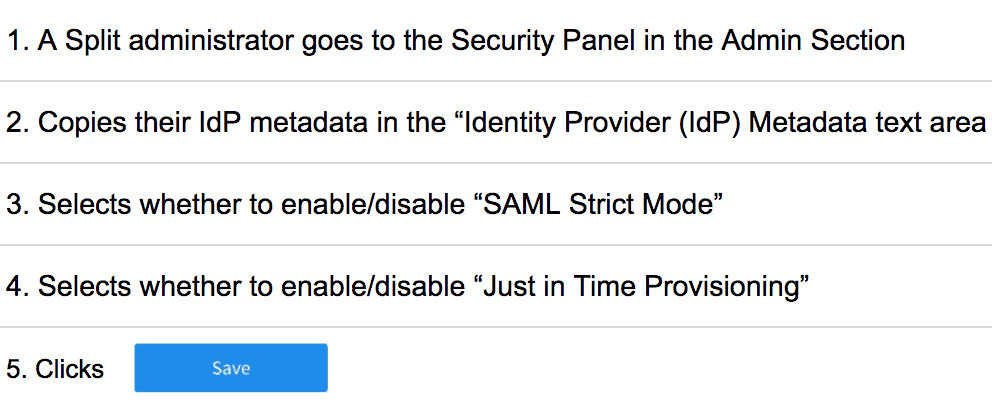
In order to configure SAML, our customers provide their IdP metadata, select a couple settings and we take it from there. We generate an Assertion Consumer Service URL and a login.
Below is a brief explanation of how to configure SAML in Split, but if you’d like, please review our official documentation.
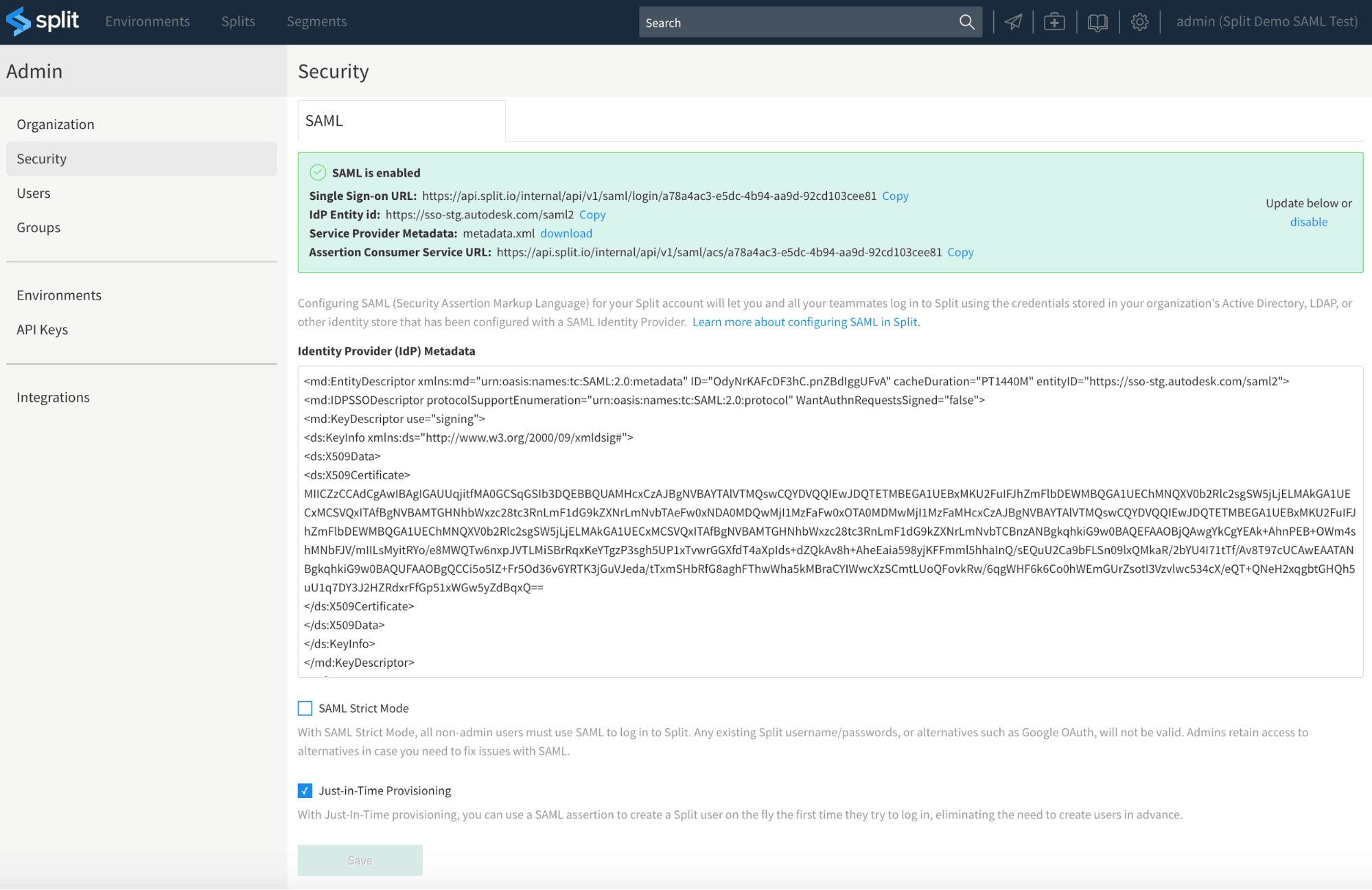
If the metadata provided is valid, Split will provide the corresponding SP endpoints in the green outlined section shown in the following image.
Supported Identity Providers
Our team has thoroughly tested Split’s SAML implementation with the following Identity Providers:
Our platform also integrates with PingFederate and SimpleSAMLphp. If your implementation requires an integration with an IdP not listed above, let us know.
References
Get Split Certified
Split Arcade includes product explainer videos, clickable product tutorials, manipulatable code examples, and interactive challenges.
Switch It On With Split
The Split Feature Data Platform™ gives you the confidence to move fast without breaking things. Set up feature flags and safely deploy to production, controlling who sees which features and when. Connect every flag to contextual data, so you can know if your features are making things better or worse and act without hesitation. Effortlessly conduct feature experiments like A/B tests without slowing down. Whether you’re looking to increase your releases, to decrease your MTTR, or to ignite your dev team without burning them out–Split is both a feature management platform and partnership to revolutionize the way the work gets done. Switch on a free account today, schedule a demo, or contact us for further questions.